We support our Publishers and Content Creators. You can view this story on their website by CLICKING HERE.

Earlier this month, former Mesa County Clerk Tina Peters was sentenced to just under nine years in prison for her ‘crimes’ in the process of making a forensic copy of the Mesa County Dominion Voting system before a “Trusted Build” was completed by the Secretary of State following a recent election.
During her trial, The Gateway Pundit was mentioned several times for publishing a video that was alleged to have published passwords. Not only were the passwords partially redacted (and useless, according to expert witness Clay Parikh) but they also should have been changed following the completion of the “Trusted Build,” which succeeded the video’s creation.
According to Mark Cook, another expert witness in the Tina Peters trial, the BIOS (Basic Input/Output System) is the first system in a computer to boot up and determines what the operating system will be configured to access.
Cook testified that with password-protected access to the BIOS, a person could “enable and disable the ability for the operating system to connect to the integrated or connected wireless card” and “turn on or turn off…the ability to attach or remove an external drive.”
Despite inaccurate claims that Peters’ actions resulted in the publishing of the BIOS passwords for the Dominion System in Mesa County, it would be deeply concerning if those passwords were, in fact, published to the public.
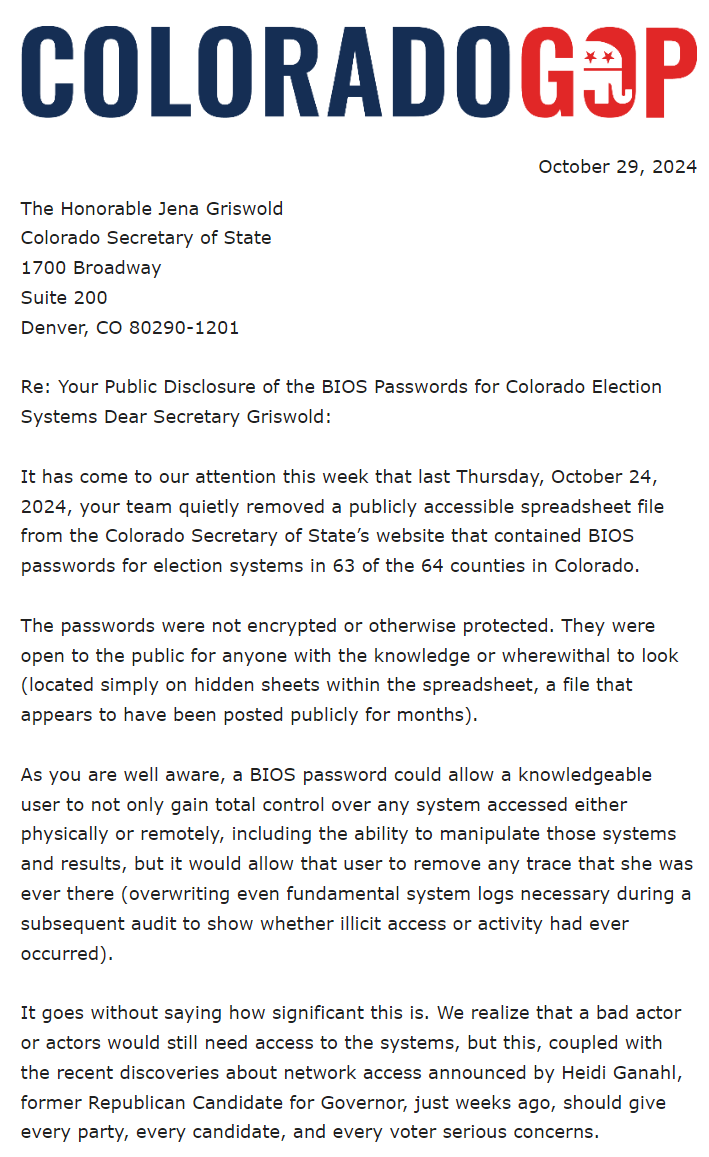
That is what the Colorado GOP believes Colorado Secretary of State Jena Griswold did from at least August 2024 until October 24, 2024.
In an email from the organization, they wrote that an affidavit they’ve received claims that Secretary of State Jena Griswold “shared a file on her website that contained over 600 BIOS passwords for voting system components of 63 out of the state’s 64 counties.”
According to the affidavit, the passwords were not encrypted or protected and were available to the public. Colorado election regulation 8 CCR 1505-1 Rule 20.5.2(c)(11) states, “The civil servants at the Department of State will securely and confidentially maintain all BIOS passwords for voting system components.”
The Colorado GOP said that this does not constitute “evidence of a breach by itself” but demonstrates a “major lapse in basic systems security and password management.” Griswold has in the past referred to Colorado elections as “The Gold Standard.”
“A bad actor would still need access either physically or remotely to the systems. It is unclear whether the passwords were in use at any point while publicly available,” the press release reads.
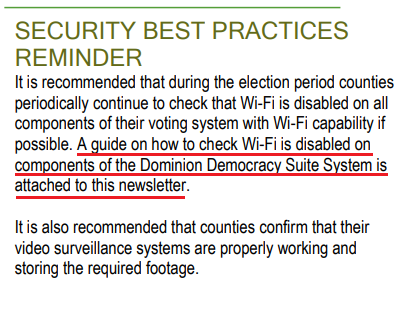
The Gateway Pundit has previously reported that a newsletter from the Secretary’s office reminds clerks to “periodically continue to check that Wi-Fi is disabled on all components of their voting system with Wi-Fi capability if possible.”
However, according to 9news, Matt Crane, a former Republican Arapahoe County Clerk and current executive director of the Colorado Clerks Association, said
“The truth is, is this a concern? Yes,” Crane said. “Is it being mitigated? Yes. Does this mean that all of the computers are connected to the internet and that votes are being flipped? No.”
It’s worth noting that The Gateway Pundit has previously reported that Crane’s wife worked for Dominion and Sequoia Voting for over a decade.
A correspondence was sent today, October 29th, 2024, to Secretary Griswold and copied to US Atty General Merrick Garland, US Atty Matt Kirsch, Chairman Sean Cooksey of the Federal Elections Commission, Governor Jared Polis, CO Atty General Phil Weiser, the Boards of County Commissioners, the CO County Clerks, and the CO Political Party Chairs, asking:
- Confirmation that all passwords disclosed have since been changed or were otherwise not current at any point while made public;
- Confirmation that all new passwords, their storage, and management meet best practices for password strength and encryption, unlike those publicly disclosed;
- Confirmation that all systems are running the current software as necessary for proper certification, as the hidden pages also provided software certification concerns;
- If the passwords were current at any point while public, confirmation that, to the best of your knowledge, the election systems have not been accessed physically or remotely by any unauthorized person or persons, including any individuals otherwise authorized to access the systems but not the system BIOS;
- Understanding that with BIOS access it may be difficult or impossible to identify if a system has been indeed compromised, provide confirmation or a detailed plan as to how all exposed systems still or will meet the certification requirements of a “trusted build” before any votes are counted by those systems in this election; and
- Provide a list of any and all other steps your team has or is taking to address these vulnerabilities, including when any steps still pending will be completed.
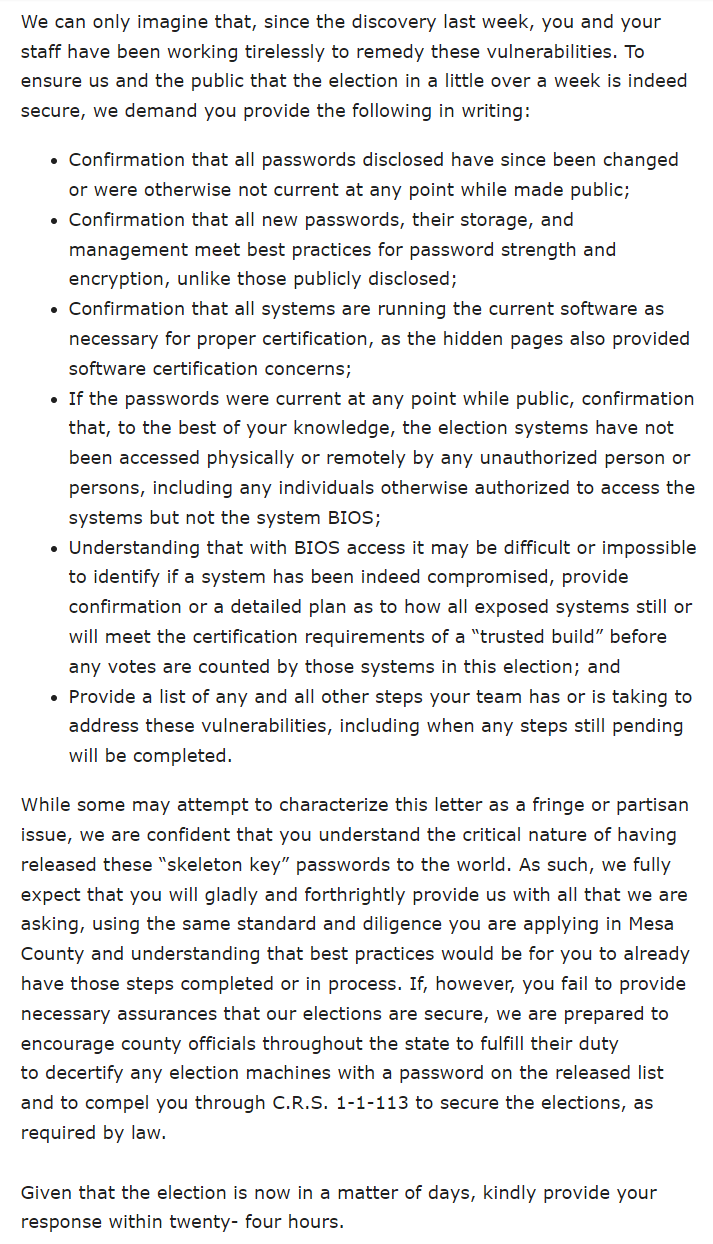
 The Colorado GOP requested the Secretary respond within 24 hours, given the proximity to the November 5th election.
The Colorado GOP requested the Secretary respond within 24 hours, given the proximity to the November 5th election.
A spokesperson for the Secretary of State’s office said that, “The Department took immediate action as soon as it was aware of this and informed the Cybersecurity and Infrastructure Security Agency (CISA), which closely monitors and protects the county’s essential security infrastructure.”
“There are two unique passwords for every election equipment component, which are kept in separate places and held by different parties. Passwords can only be used with physical in-person access to a voting system.”
The Lindell Offense Fund has released the following:


 Conservative
Conservative  Search
Search Trending
Trending Current News
Current News 


